We're sorry, but we couldn't find any results that match your search criteria. Please try again with different keywords or filters.
Loading
-
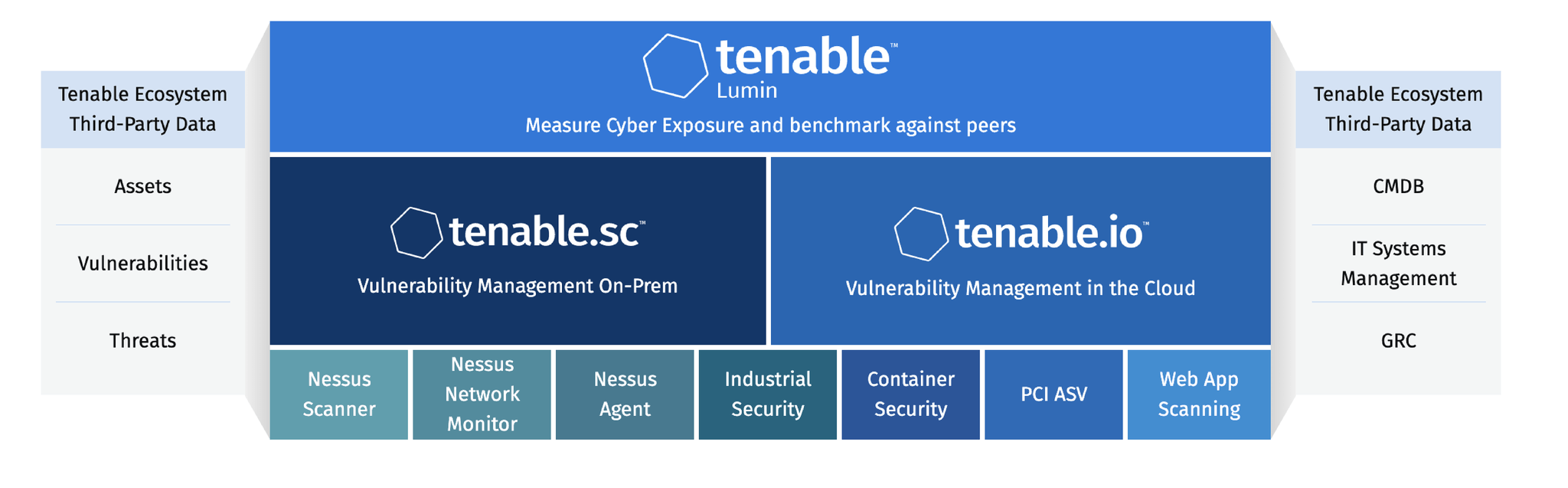
The Tenable Cyber Exposure platform is the industry’s first solution to holistically assess, manage and measure cyber risk across the modern attack surface.
-
Comprehensive study of 100 business decision makers in Singapore reveals the role corporate culture and employee education play in successful cybersecurity practices
-
New York, NY (July 30, 2019) – AppViewX, an emerging leader in the automation and orchestration of network infrastructure for large enterprises, today announced it has secured $30 million in growth fu ...
-
A £183m fine was not what the directors of British Airways (BA) had been expecting. Owing to the GDPR, data breaches can end up being quite expensive— something the UK airline is now discovering for i ...
-
Currently, most IoT devices use RSA and ECC to protect confidentiality, integrity and authenticity for device identities and communication. Experts from the security community, including Dr. Brian LaM ...
-
Utimaco, a leading manufacturer of Hardware Security Module (HSM) technology, received the Common Criteria (CC) EAL4+ certification for its CryptoServer CP5 HSM based on the eIDAS Protection Profile E ...
-
Incident Resolution Automation and Orchestration technologies promise to work smarter, faster and more efficiently despite the limited resources your team might be operating under.
-
Indeed Identity understands that the issue of controlling privileged access might be CISO’s headache. Lack of control over admin accounts, impossibility to investigate incidents connected with the mis ...
-
CIOReview Magazine recently recognized CyberInt as one of 2018’s 20 Most Promising Enterprise Security Solution Providers. The yearly recognition - reviewed by a distinguished panel of CEOs, CIOs, CIS ...
-
According to the annual report of the White House economic advisers to the President of the United States, the Internet and the large-scale piracy that it carries represent one of the greatest threa ...
-
For companies, government bodies or even individuals, data security is one of the most important elements as it relates to internal secrecy. However, hackers seem to have many ways to break the data ...
-
New File Delete’ feature strengthens Cb Protection as a direct control for PCI DSS requirement 5, enabling customers to replace legacy antivirus without the need for compensating controls.


 Cloud & AI Infrastructure
Cloud & AI Infrastructure
 eCommerce Expo | DMEXCO ASIA
eCommerce Expo | DMEXCO ASIA







)
)
)
)
)
)
)
)
)
)
)
)
)
)
)
)
)
)
)
.png/fit-in/1280x9999/filters:no_upscale())
)
)
)
)
)
)
)
)
)
)
)
)
)
)
)
)
)
)
